The House of Representatives just passed a resolution to nullify an FCC rule which should cause concern for all Internet denizens. The FCC rule in question prevented Internet Service Providers (ISPs) from collecting information about your Internet activities and selling that data. Now, companies like Verizon, Comcast, Time Warner, and anybody who provides Internet access, can gather your browsing history, video watching history (via Deep Packet Inspection), email, or anything else that passes through their infrastructure unencrypted*.
How does my ISP know about all my data?

When you visit a website (let’s say this one!) two things happen:
- Your computer turns the website name into an Internet Protocol (IP) address by making a DNS query. example: zimventures.com => 96.126.111.96
- Your computer connects to the resolved address and requests a webpage
In both of those steps, your ISP receives the data from your computer and shuttles it along to the next hop along the Internet. If the site you’re visiting uses encryption, the data transferred between your computer and the website (step 2) won’t be easily snooped on.
Let’s say that the site you’re visiting does use encryption (great!). There’s only one problem: in step 1, you asked to resolve the name of that website, and that operation is completely in the clear. Your ISP still knows what site you’re going to.
How Can I Minimize The Snooping?
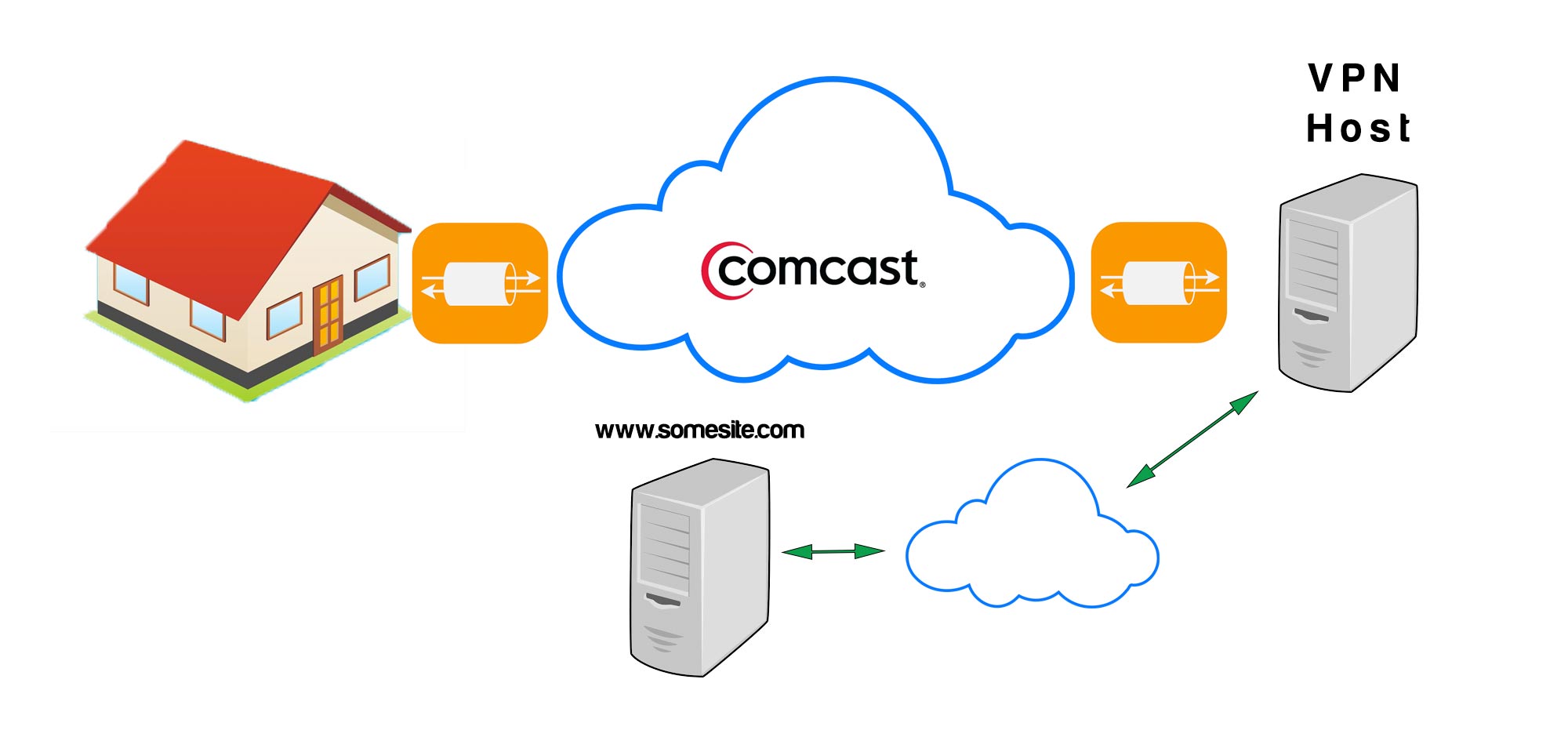
By encrypting ALL of your outbound data, you can minimize the chances that your ISP will be harvesting data when it shouldn’t be. How does one encrypt all outbound data? By using a Virtual Private Network (VPN). Usually, most people associate VPN technology with a secure connection they use to connect to their office from home.
In this scenario, your computer creates an encrypted permanent connection to a remote host, but it isn’t your office. ALL traffic from your computer will travel over that link to a remote VPN provider. Of course, the caveat here is that you’re now shifting your trust to whomever your VPN provider is. They will decrypt the traffic when it arrives, and then forward it out to the Internet. The assumption here is that they’re not snooping! Be sure your VPN provider explicitly says they do not log traffic or resell data.
VPN Termination Points
It’s important to note here that your ISP sees ALL traffic coming out of your connection. That means you have two options to secure your outbound traffic:
- Install VPN clients on every computer/device in your house
- Setup a VPN termination point on your home’s router
Most VPN providers will provide instructions on installing their software on your computers. Installing one on your home router is a far more complicated endeavor (depending on your router) but will secure all outbound traffic. As mentioned earlier: this will encrypt all traffic and there are downsides to doing so!
Change your DNS resolver
Another important caveat here is that you shouldn’t be using your ISP’s DNS service. When your computer needs to translate a website name into an IP address, it should be using other services such as OpenDNS.
Downsides of VPN technology
By shipping all your traffic over an encrypted tunnel to a remote host, you’ve essentially added an extra step for your request to reach its destination. This adds extra time to your round trip which is usually on the order of milliseconds. Not a big deal when you’re browsing the web but a VERY big deal when you’re gaming. Do you really care that your ISP knows you play World of Warcraft? Don’t worry, your secret is safe with me.
Also, some websites (most notably, Netflix) don’t allow you to use their services through a VPN. They can detect the IP address you’re connecting from and reject your request because they don’t physically know where you’re connecting from. They have valid reasons for doing so, but it’s a major inconvenience for customers who are legitimately using their service.
What else is a VPN good for?
Another great use case for VPN technology is to prevent snooping while you’re on public WIFI connections. Say you’re sitting at Starbucks, working on your third latte (CAFFEINE RULES!!!!). Just like in the scenario where your ISP can see all your traffic, anyone else on the same public WIFI can also see your traffic. Encrypt it all and ship it over your VPN connection instead!
Perhaps your workplace offers a public WIFI access point. Do you really want your employer to have the ability to log all your website traffic? I’ll ignore the fact you should be working….slacker. Ship those packets of data over your VPN connection instead!
Bottom Line
VPN technology can help ensure your data stays private and can help prevent ISPs from monetizing your behavior. However, it’s sad that it’s come to this stage. Users are actually PAYING for a service and that service is not only making money from the users, but also the users behaviors. The ISP monopolies are absolutely pillaging the Internet for every dime it’s worth. A far cry from the days of dial-up when ISPs were your access points to the “Information Superhighway”.
*Technically, ISP’s could run a man-in-the-middle “attack” and decrypt all your traffic.
